Peter O'Brien
tnsping without the TNSNAMES.ORA entry
It isn't immediately obvious in the tnsping documentation, but it is possible to perform the ping without having the Transparent Network Substrate configuration in place (i.e net service name) on the client for the database in question.
$ORACLE_HOME/bin/tnsping <hostname>:<port>/<sid>
$ORACLE_HOME/bin/tnsping <hostname>:<port>/<sid>
Tailoring Fusion CRM
The journey for the Fusion CRM development team has been a long one. What a great feeling for all of us when Fusion Applications was officially released this year as Generally Available. During his keynote speech at this year's Oracle OpenWorld Steve Miranda reiterates that statement. Also during his session there were some great demonstrations of Fusion CRM. Anthony Lye demonstrated (about 25 minutes into the presentation) how the application can be extended at run time. Design time at run time features are made possible by a number of Fusion Middleware technologies including WebCenter and MDS (pdf 592kb). Extending the application, as Anthony Lye demonstrated, is one form of tailoring that can be performed with the out of the box application. Other forms of tailoring include personalisation and customisation (personalization and customization in the documentation). Both concepts are very similar in that changes to the application are persisted via MDS but they are differentiated by the scope of the change and for whom the change is made.
 Available to all users.Put simply, personalisation is a tailoring action performed by an end user for themselves to set their own preferences for how they work with the application. These changes can be to include dynamic content such as Business Intelligence reports or a syndication feed from an external source. The key point is that these are personal preferences explicitly specified by the user for the user by editing the page via the WebCenter Page Composer. A user can also perform implicit personalisation of the Fusion CRM application without ever touching Page Composer simply by hiding columns in a table, or rearranging their order relative to each other by dragging and dropping. These personal preferences are also reflected in the shared components across Fusion CRM including the Activities UI components for Notes, Interactions, Appointments and Tasks. Setting a preference for the display width of the comments column for Tasks in the Marketing application is reflected in Opportunity Management.
Available to all users.Put simply, personalisation is a tailoring action performed by an end user for themselves to set their own preferences for how they work with the application. These changes can be to include dynamic content such as Business Intelligence reports or a syndication feed from an external source. The key point is that these are personal preferences explicitly specified by the user for the user by editing the page via the WebCenter Page Composer. A user can also perform implicit personalisation of the Fusion CRM application without ever touching Page Composer simply by hiding columns in a table, or rearranging their order relative to each other by dragging and dropping. These personal preferences are also reflected in the shared components across Fusion CRM including the Activities UI components for Notes, Interactions, Appointments and Tasks. Setting a preference for the display width of the comments column for Tasks in the Marketing application is reflected in Opportunity Management.
 Only available to users with Administration privileges.In the context of Fusion CRM, customisation is a modification made by an administrator, or someone with the appropriate permissions, to the application for a set of users. This set, referred to as Customization Level, can be defined as all users for the installed application, internal users, external users or users with a particular set of roles. For the Partner Relationship Management functionality in Fusion CRM V1 the internal vs external layer was introduced so that a Channel Administrator could tailor how they wanted their partners (external users) to see the Fusion CRM screens. Both internal and external users are interacting with the same screen, but the external users may see a lot more branding and content more suitable for partners rather than employees.
Only available to users with Administration privileges.In the context of Fusion CRM, customisation is a modification made by an administrator, or someone with the appropriate permissions, to the application for a set of users. This set, referred to as Customization Level, can be defined as all users for the installed application, internal users, external users or users with a particular set of roles. For the Partner Relationship Management functionality in Fusion CRM V1 the internal vs external layer was introduced so that a Channel Administrator could tailor how they wanted their partners (external users) to see the Fusion CRM screens. Both internal and external users are interacting with the same screen, but the external users may see a lot more branding and content more suitable for partners rather than employees.
From a development perspective, MDS terminology can make things a bit confusing because irrespective of the nature of change, MDS refers to it as a customisation. There are many cross platform components used in Fusion CRM that are individual products in themselves. Getting to grips with the terminology used by these different product teams and understanding the context has been a challenge, but really rewarding when you see the results.
From a development perspective, MDS terminology can make things a bit confusing because irrespective of the nature of change, MDS refers to it as a customisation. There are many cross platform components used in Fusion CRM that are individual products in themselves. Getting to grips with the terminology used by these different product teams and understanding the context has been a challenge, but really rewarding when you see the results.
Multi Byte String Generator
It has a simple interface where you specify the number of bytes you want per character (1 to 3) and what the number of characters you want. The randomly generated string is displayed and you can copy it to your clipboard (using the Copy to Clipboard button) and paste it into your application or test fixture. Due to the security features of Java Web Start, you will be prompted to allow the application to access your local clipboard. Some additional information about how many bytes the string occupies in UTF-8, UTF-16 and UTF-32 encoding is also displayed.
Using OSGi to explain the difference between Factory and Broker pattern

Peter's explanation makes it very clear why Factory is good, but just not good enough, for enterprise applications. I hope he contributes more on the series.
Irish software at Oracle OpenWorld 2010
Preparation for the trio of Oracle's major conferences (Oracle OpenWorld, JavaOne, Oracle Develop) has been underway for months, but once September comes around the pace really quickens. The final touches get put to product demonstration scripts, keynote speeches, and honing the elevator pitch. In product development you know it's September because you can not find a product manager without scheduling a meeting days in advance. Of course, this is not unique to Oracle. There will be over 300 exhibitors at Oracle OpenWorld and many of them will be making sure their product or service is presented in the best possible manner. Having announced a major certification over the summer with Oracle's Global License Management Services, the staff at one Irish software company will be no different.
iQuate is an Irish software company which produces network inventory and network management solutions for large, complex networks. Using a multitude of protocols iQuate queries PCs, servers, network devices, databases to not only build up a profile of what is installed, but also what is actually being used. This information allows companies to potentially save a fortune on their software licencing fees, by simply not paying for what they are not using. Check them out at stand 3130 in the Moscone Center, West Exhibition Hall, Level 1.
Come to thing of it, Oracle has development centres around the world and the Dublin offices have staff working on server technology, tools and application software. So some portions of the Oracle software on show will have been made in Ireland too! :-)
Is iQuate really the only Irish software company exhibiting? It is the only one on the list of exhibitors with an Irish HQ. There might be other software companies that originated in or do the majority of their development in Ireland but have not listed an Irish address as their headquarters when registering as an exhibitor. In an effort to get into the US market and not appear as a foreign company, some businesses move their HQ to the US. This also demonstrates their commitment to the market. If you know of any other Irish software companies exhibiting this year please let me know and I would be delighted to include them.
ADF logging level to see SQL statements
Very handy for debugging runtime issues when developing, the Oracle ADF Business Components layer can output the SQL that it is executing. To do this though, the logging threshold must be set to a specific level...
'-Djbo.debugoutput=console -Djbo.logging.trace.threshold=5'
Curiously. the SQL statements do not get displayed for any other threshold level.
'-Djbo.debugoutput=console -Djbo.logging.trace.threshold=5'
Curiously. the SQL statements do not get displayed for any other threshold level.
Loosely typed interfaces - The Normalizer Pattern and Oracle SOA Suite
When getting two or more systems working together, the making a connection part is generally the easiest, identity propagation is a bit trickier, but many times, the syntax and semantics of one system is at odds with another one. Over the decades this has been manifest in many ways and thankfully there are tools and techniques to work through them. A collation of such techniques is Enterprise Integration Patterns. The book, along with the associated website, is worthy of a dedicated article or two, and is not the real subject of this article. One message transformation pattern the book describes is the Normalizer Pattern where different formats for essentially the same object are catered for.
An example where this form of message translation becomes necessary is when using a service with a loosely typed interface. This can often happen when an existing system or utility (such as a batch / command processor) gets exposed as a web service. The request / response payload is little more than a collection of key / value pairs. There are a couple of ways to cater for this using Oracle SOA Suite 11g which I will outline in this article. One has full tool support. The other, a solution using XSLT, is not fully supported, but has an advantage in that the XSLT can be used both with the BPEL and Mediator components.
Troublesome Payloads
The challenge is to get something that is strongly typed into something that is loosely typed
Strongly TypedLoosely Typed
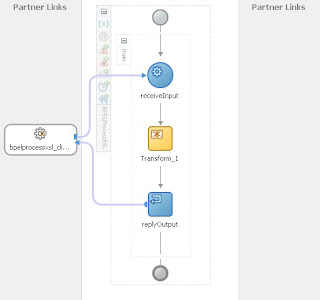
BPEL assign with copy and insertAfter
You can cater for the key / value pair structure by repeatedly appending a new 'property' element and then, using an XPATH predicate to specify which 'property' element is the target, copying the desired values. In the BPEL process this can all be done in a single 'assign' command, using the insertAfter instruction from the Oracle BPEL extension library. The BPEL designer supports this approach, and it is used extensively in production systems around the globe. It can get difficult to maintain and hard to read if the payload is large though. If dealing with a large payload see if you can split the copy / insertAfter instructions into two or more 'assign' commands. Ideally, you would give these 'assign' commands logical names such as 'assign_part_1_admin_details' and 'assign_part_2_finance_details'. What is a large payload in this case then? Well, I would say that if you have more than 10 key value pairs you should be seriously thinking about splitting them up and if you have more than 20, you should be definitely splitting them up. Remember, you might be familiar with the structure and understand how it is constructed, but what about the college graduate brought in by the consulting firm in a months time, or even you having to come back to this in 6 months time? Go on, make the maintenance a bit easier for everyone and break that assign behemoth into manageable chunks!
BPEL transform with XSLT
If experienced in dealing with XML documents then this approach will probably be very familiar to you. Extensible Stylesheet Language Transformations is used to convert XML data into some other format, which may also be XML data. In this case the stylesheet explicitly describes the target XML structure, making it somewhat easier to read than the BPEL assign approach described earlier. For example...
Which one is right for me?
As one can see from the diagrams there is not much difference in the BPEL designer between the two examples and the decision on which technique to use would be based on factors which are different from company to company, but clearly use of the XSL mapper is an important factor.
The complete example application with SOA composite is available at http://sites.google.com/site/soastation/soastation_looselytyped_normalizer.zip
An example where this form of message translation becomes necessary is when using a service with a loosely typed interface. This can often happen when an existing system or utility (such as a batch / command processor) gets exposed as a web service. The request / response payload is little more than a collection of key / value pairs. There are a couple of ways to cater for this using Oracle SOA Suite 11g which I will outline in this article. One has full tool support. The other, a solution using XSLT, is not fully supported, but has an advantage in that the XSLT can be used both with the BPEL and Mediator components.
Troublesome Payloads
The challenge is to get something that is strongly typed into something that is loosely typed
Strongly TypedLoosely Typed
<department>
<name>Furniture</name>
<manager>Pam Beech</manager>
<budget>50000</budget>
<spent>20000</spent>
<committed>47000</committed>
</department>
<property>Now this is quite a simple example and the real world has a lot more complicated cases out there. Ones that would involve number formatting, character encoding, attribute concatenation, and so on. For the purposes of this exercise however, it is ideal to illustrate the point. All the files in this example are free and available for you to use, modify or incorporate into your own solution as you see fit. The example was produced and tested using Oracle Fusion Middleware 11.1.1.2.0. That is JDeveloper Studio 11.1.1.2.0 and WebLogic Server 11gR1. To reduce the number of files and dependencies involved, the example is a simple service (BPELProcessExample.wsdl) that takes a strongly typed request payload and returns a loosely typed response payload. The SOA composite project contains two BPEL processes that provide slightly different implementations for this same WSDL.
<key>NAME</key>
<value>Furniture</value>
</property>
<property>
<key>MANAGER</key>
<value>Pam Beech</value>
</property>
<property>
<key>BUDGET</key>
<value>50000</value>
</property>
<property>
<key>SPENT</key>
<value>20000</value>
</property>
<property>
<key>COMMITTED</key>
<value>47000</value>
</property>
BPEL assign with copy and insertAfter
You can cater for the key / value pair structure by repeatedly appending a new 'property' element and then, using an XPATH predicate to specify which 'property' element is the target, copying the desired values. In the BPEL process this can all be done in a single 'assign' command, using the insertAfter instruction from the Oracle BPEL extension library. The BPEL designer supports this approach, and it is used extensively in production systems around the globe. It can get difficult to maintain and hard to read if the payload is large though. If dealing with a large payload see if you can split the copy / insertAfter instructions into two or more 'assign' commands. Ideally, you would give these 'assign' commands logical names such as 'assign_part_1_admin_details' and 'assign_part_2_finance_details'. What is a large payload in this case then? Well, I would say that if you have more than 10 key value pairs you should be seriously thinking about splitting them up and if you have more than 20, you should be definitely splitting them up. Remember, you might be familiar with the structure and understand how it is constructed, but what about the college graduate brought in by the consulting firm in a months time, or even you having to come back to this in 6 months time? Go on, make the maintenance a bit easier for everyone and break that assign behemoth into manageable chunks!
BPEL transform with XSLT
If experienced in dealing with XML documents then this approach will probably be very familiar to you. Extensible Stylesheet Language Transformations is used to convert XML data into some other format, which may also be XML data. In this case the stylesheet explicitly describes the target XML structure, making it somewhat easier to read than the BPEL assign approach described earlier. For example...
<client:property>The 'client' is a namespace prefix for the schema and in this SOA composite example the request and response happen to be defined in the same schema. This is easier to read, even if one is not all that familiar with XSL. For large payloads it is not necessary to split up the transformation as one might consider for the BPEL assign, but it could be done. The single transformation file could have a whole set of templates. However, the XSL Mapper does not support this approach yet, so if using this approach you will have to work in the Source editor, not the Design mode. Since this is using XSLT, the same XSL file can be used by the Mediator too, so it is not only a BPEL solution.
<client:key>
<xsl:text disable-output-escaping="no">MANAGER</xsl:text>
</client:key>
<client:value>
<xsl:value-of select="/client:process/client:department/client:manager">
</xsl:value-of>
</client:value>
</client:property>
Which one is right for me?
As one can see from the diagrams there is not much difference in the BPEL designer between the two examples and the decision on which technique to use would be based on factors which are different from company to company, but clearly use of the XSL mapper is an important factor.
The complete example application with SOA composite is available at http://sites.google.com/site/soastation/soastation_looselytyped_normalizer.zip
The Art of Agile Development
 Keep this book to handThe Art of Agile Development was recommended to me by Jeff McKenna when he provided some Scrum coaching to those of us in the Dublin office working on Oracle Social CRM. Back then it was a new, hot off the press book, but I have recently reread it because I have found it useful in providing guidance on what to watch out for when changing agile development practices. This was necessary due to changes in teams and technologies as some of us focused full time on Fusion Applications. Practices, roles and responsibilities we had gotten used to had to be adapted or dropped to blend in with APM, Oracle Fusion Application's development methodology.
Keep this book to handThe Art of Agile Development was recommended to me by Jeff McKenna when he provided some Scrum coaching to those of us in the Dublin office working on Oracle Social CRM. Back then it was a new, hot off the press book, but I have recently reread it because I have found it useful in providing guidance on what to watch out for when changing agile development practices. This was necessary due to changes in teams and technologies as some of us focused full time on Fusion Applications. Practices, roles and responsibilities we had gotten used to had to be adapted or dropped to blend in with APM, Oracle Fusion Application's development methodology.The book, by Shane Warden and James Shore, is a great introduction to agile development methodologies by covering both XP and scrum. Practical examples are generally from XP projects because that is where the authors have the greatest experience. The authors identify a broad set of practices that would be considered as characteristics of agile development methodologies in way or another. Recognising that it is very rare in most organisations to be able to follow an agile methodology completely as prescribed alternatives are mentioned, but not in every case. Shane and James are also very clear that many of these practices are often taking place at the same time in a software project rather than in a sequential waterfall methodology. However, categorising practices by what sort of activity and the nature of the activity give a very useful matrix for teams to analyse how agile their own practices are and perhaps identify areas where realistic improvements can be made. Just being able to have a label or term for a specific practice makes discussing within a group easier.
 Download poster from James ShoreI see the collection of practices being grouped by nouns (planning, analysis, design & coding, testing, deployment) and verbs (thinking, collaborating, releasing, planning, developing). For example, when team members are working on implementing a specific feature that kind of collaboration is 'design & coding collaborating' and the section in the book covers some pair programming techniques. In fact, this particular section addresses the misconception that pair programming is a fulltime 'paired for life' regime. It is a useful tool that can be used for a few hours a day to make some significant progress, reduce interruptions, and spread the knowledge of how and why parts of the system being developed work.
Download poster from James ShoreI see the collection of practices being grouped by nouns (planning, analysis, design & coding, testing, deployment) and verbs (thinking, collaborating, releasing, planning, developing). For example, when team members are working on implementing a specific feature that kind of collaboration is 'design & coding collaborating' and the section in the book covers some pair programming techniques. In fact, this particular section addresses the misconception that pair programming is a fulltime 'paired for life' regime. It is a useful tool that can be used for a few hours a day to make some significant progress, reduce interruptions, and spread the knowledge of how and why parts of the system being developed work.Other useful techniques peppered through the book include the Agility Self Assessment and the many skill development routines, which the authors called 'etudes'. These are short exercises that may help in getting the feel for a more agile approach. When reading the chapters you might be thinking we don't have the development experience to let team members do organic, incremental architecture design, or implement thorough automated testing. I wonder how many people never complete the book because they do not believe they can carry out these changes and deliver software in a timely fashion. It's not until towards the end of the book that the authors address the reality of the mixed capabilities of the team. If this was at the beginning it might give the readers more staying power. The book does have some helpful advice on working with and around the politics, the mixture in experience levels, and heavy weight project management within your organisation. It has to be read in it's entirety though and does make for an excellent reference book to dip in and out of.
This article has been edited since it was first published.
Should we ban anonymity on the Internet?
In an Information Security article a few months back, Bruce Schneier (author of Schneier on Security ) and Marcus Ranum put some points forward for and against internet anonymity. I have to admit that I agree with Schneier and find Ranum's argument quite weak. He appears to suggest that the main reason to enforce identity is to avoid spam. The tools aren't great, but there are already mechanisms in place to address this. Criminals are always getting better at finding ways to exploit weaknesses in internet technologies increasingly at the heart of the way we shop, interact, work, entertain and inform ourselves. We just have to keep up with the pace in the cat and mouse game. Sacrificing anonymity, and the right to privacy, is too great a cost for just avoiding emails about Viagra (tm) and Nigerian generals with a stash of cash to move out of the country.
) and Marcus Ranum put some points forward for and against internet anonymity. I have to admit that I agree with Schneier and find Ranum's argument quite weak. He appears to suggest that the main reason to enforce identity is to avoid spam. The tools aren't great, but there are already mechanisms in place to address this. Criminals are always getting better at finding ways to exploit weaknesses in internet technologies increasingly at the heart of the way we shop, interact, work, entertain and inform ourselves. We just have to keep up with the pace in the cat and mouse game. Sacrificing anonymity, and the right to privacy, is too great a cost for just avoiding emails about Viagra (tm) and Nigerian generals with a stash of cash to move out of the country.
What is the great danger of not being anonymous? Well it's all the inferring that goes on about facts that get gathered around the things you search for, shop for, chat about, view and listen to. These are then used to categorise you for advertising, inclusion or exclusion from groups or activities. NetFlix provided a great example of this last year. Just weeks after the contest began, two University of Texas researchers showed that with the NetFlix data one could identify users and in some cases their political leanings and sexual orientation.
Read more about that at: http://www.wired.com/threatlevel/2009/12/netflix-privacy-lawsuit/#ixzz0oZfNuAqb
Getting back to Schneier's point, trying to implement a robust identification system, which criminals can not outwit or take advantage of, is not possible...
Mandating universal identity and attribution is the wrong goal. Accept that there will always be anonymous speech on the Internet. Accept that you'll never truly know where a packet came from. Work on the problems you can solve: software that's secure in the face of whatever packet it receives, identification systems that are secure enough in the face of the risks. We can do far better at these things than we're doing, and they'll do more to improve security than trying to fix insoluble problems.
What is the great danger of not being anonymous? Well it's all the inferring that goes on about facts that get gathered around the things you search for, shop for, chat about, view and listen to. These are then used to categorise you for advertising, inclusion or exclusion from groups or activities. NetFlix provided a great example of this last year. Just weeks after the contest began, two University of Texas researchers showed that with the NetFlix data one could identify users and in some cases their political leanings and sexual orientation.
Read more about that at: http://www.wired.com/threatlevel/2009/12/netflix-privacy-lawsuit/#ixzz0oZfNuAqb
Getting back to Schneier's point, trying to implement a robust identification system, which criminals can not outwit or take advantage of, is not possible...
Mandating universal identity and attribution is the wrong goal. Accept that there will always be anonymous speech on the Internet. Accept that you'll never truly know where a packet came from. Work on the problems you can solve: software that's secure in the face of whatever packet it receives, identification systems that are secure enough in the face of the risks. We can do far better at these things than we're doing, and they'll do more to improve security than trying to fix insoluble problems.
More than Iron Man - Oracle and Marvel
At the beginning of April 2010, Oracle, using the buzz around the release of Iron Man 2, kicked off a worldwide advertising campaign focused on introducing the powerful combination of Oracle and Sun. This includes old school billboards and commercials on a variety of old and new media platforms...
All this makes for some fantastic visuals, but how exactly is Marvel using Oracle? The list of Oracle products being used by Marvel is diverse:
All this makes for some fantastic visuals, but how exactly is Marvel using Oracle? The list of Oracle products being used by Marvel is diverse:
- Oracle E-Business Suite, including Financials, Human Resources, Self Service HR, Manufacturing and Incentive Compensation
- Oracle Business Intelligence Suite
- Oracle Configurator
- Oracle Enterprise Content Management Suite (formerly Stellent)
- Oracle Insight
Interface Oriented Design
 This book has been sitting on my desk for a long time and I've been dipping in and out of it for at least a year. I'm a big fan of The Pragmatic Programmers and the topic of interface is very close to my heart as it is often the most ignored when system analysis and design occurs. Apart from performance, interfaces are generally the biggest problem that is faced when a system goes live because once people start to use it, they want to use it with the other systems and tools they are using. The human interface to a computer system gets, quite rightly, a lot of focus. The topic gets it's own module in Computer Science degree courses. This has meant that today's software developer is familiar with the concepts of usability, task analysis, workspace arrangement, error detection and recognition.
This book has been sitting on my desk for a long time and I've been dipping in and out of it for at least a year. I'm a big fan of The Pragmatic Programmers and the topic of interface is very close to my heart as it is often the most ignored when system analysis and design occurs. Apart from performance, interfaces are generally the biggest problem that is faced when a system goes live because once people start to use it, they want to use it with the other systems and tools they are using. The human interface to a computer system gets, quite rightly, a lot of focus. The topic gets it's own module in Computer Science degree courses. This has meant that today's software developer is familiar with the concepts of usability, task analysis, workspace arrangement, error detection and recognition.I was hoping that Ken Pugh's Interface Oriented Design was going to be that seminal book which would set out design principles and approaches for deriving robust interfaces. It is not. While it does introduce some interesting concepts such as the Three Laws of Interfaces and Interface Responsibility Interaction it lacks a real world sense about it. In fact, the purpose of the book appears to be the platform to launch Pugh's Interface Responsibility Interaction format. It's an interesting idea, but unfortunately it does not make a strong case for using such a format in real projects. Some case studies from other projects where IRI was used would have been beneficial.
One gets the sense that this is a serialisation of some lectures within a system design module in college, with a trivial exercise to prove the points. Put simply, there's really not much in the book to grab the experienced developers attention.
It's not you, it's me - Check the bugs log before going crazy

How many times have you been working on implementing, unsuccessfully, a feature in your application which relies on a framework, container, or some other indirection layer? You've studied the specifications, memorised the API and you're following the developers guide which are all telling you that what you are trying to implement is taken care of, but it still does not work!
While recently working on a really simple application feature using ADF data model validation I had just this experience. The feature just did not work and there was nothing in the logs to indicate what the problem was or that there was even a problem. Admittedly, I was using an internal development build, so it would not have been a fully tested version. I checked, and double checked everything, the documentation, searched through forums and blogs, trying to find out what I was doing wrong.
By the way, while searching I did come across an interesting blog about ADF bugs and workarounds. Steve Muench's Dive into ADF blog is probably the most comprehensive on ADF features though.
It turned out I wasn't doing anything wrong but I only found this out when a colleague suggested I check the bugs database. And there it was! The exact scenario I was trying to implement had a bug against it. What a relief, because I thought I was missing or skipping over something really obvious and fundamental and that's why it wasn't working for me. Better still, the defect was marked as closed so it will be available in the next internal developers build.
This got me thinking about all the documentation sources I had been to and how useful it would be to have a cross reference between the structured and unstructured text of developer guides, API, forums, blogs and bug databases. Isn't that what search engines are for?
Unit Testing with SQL Developer
December's release of SQL Developer 2.1 has a number of new bells and whistles. Two of the main new features are:
http://www.oracle.com/technology/obe/11gr2_db_prod/appdev/sqldev/sqldev_unit_test/sqldev_unit_test_otn.htm
- Data Model Viewer. This is a free, read only, viewer based on Oracle SQL Developer Data Modeler. With this viewer you can open existing data models as well as generate data models based on your database. The generated data model can not be saved though.
- Unit Testing. Based on the popular xunit Four Phase Test pattern, this feature makes testing of procedures and functions a breeze. Put simply, it allows one to construct a repository of unit tests cases which includes what one would expect for automated testing: setup, execute, assert result, record results, teardown.
http://www.oracle.com/technology/obe/11gr2_db_prod/appdev/sqldev/sqldev_unit_test/sqldev_unit_test_otn.htm
Your ScrumMaster is a project manager in disguise
In 6 attributes of a good ScrumMaster Mike Cohn repeats the common line that the ScrumMaster role does not always require a full-time, eight-hour-a-day commitment. Often the 'orchestra conductor' role of ScrumMaster is an unofficial one within your organisation even though it clearly has well defined functions and responsibilities. So many people do ask the question Is a ScrumMaster a full time position? As Boris points out, it is, and he explains why it is a 100% fulltime job.
The ScrumMaster has internal and external responsibilities. Even if the team is well disciplined with following the process, and they address most of their own impediments there is still the challenge of being a gatekeeper between the management and the team. This is being recognised in many organisations now and you can even see ScrumMaster as a recruitment position. It's interesting to note that many of these positions have Project Manager / ScrumMaster as the title.
 What does a Project Manager do that a ScrumMaster does not (or vice versa)? A project manager is the person who has the overall responsibility for the successful planning and execution of a project. This title is used in the construction industry, architecture, information technology and many different occupations that are based on production of a product or service. While strictly speaking, the team, rather than the ScrumMaster has responsibility for the success of the project, a ScrumMaster does assume responsibility for the team’s adoption of Scrum and practice of it. A ScrumMaster takes on this responsibility without assuming any of the power that might be useful in achieving in it.
What does a Project Manager do that a ScrumMaster does not (or vice versa)? A project manager is the person who has the overall responsibility for the successful planning and execution of a project. This title is used in the construction industry, architecture, information technology and many different occupations that are based on production of a product or service. While strictly speaking, the team, rather than the ScrumMaster has responsibility for the success of the project, a ScrumMaster does assume responsibility for the team’s adoption of Scrum and practice of it. A ScrumMaster takes on this responsibility without assuming any of the power that might be useful in achieving in it.
To boil it all down to it's essence, a ScrumMaster is a Project Manager who has realised that they don't really have the power to successfully deliver a project, and has adopted a framework to take advantage of that humbling position.
The ScrumMaster has internal and external responsibilities. Even if the team is well disciplined with following the process, and they address most of their own impediments there is still the challenge of being a gatekeeper between the management and the team. This is being recognised in many organisations now and you can even see ScrumMaster as a recruitment position. It's interesting to note that many of these positions have Project Manager / ScrumMaster as the title.
To boil it all down to it's essence, a ScrumMaster is a Project Manager who has realised that they don't really have the power to successfully deliver a project, and has adopted a framework to take advantage of that humbling position.
Oracle VPN
 Virtual Private Networks have made remote working and access to critical corporate resources so much easier over the past few years. In fact, there is so much about the way we work today that is dependent on being able to get at data remotely yet in a secure manner. The VPN diagram to the left provides a simple representation of what a VPN does. It creates a secure tunnel (red lines) for the transfer of data (green line) between two points.
Virtual Private Networks have made remote working and access to critical corporate resources so much easier over the past few years. In fact, there is so much about the way we work today that is dependent on being able to get at data remotely yet in a secure manner. The VPN diagram to the left provides a simple representation of what a VPN does. It creates a secure tunnel (red lines) for the transfer of data (green line) between two points.So what do you do when you need to get some work done, but you've got your corporate laptop safely and securely locked in a drawer in the office?
There is a website for Oracle employees that has software downloads, remote access tools, patches and so on. It is called Oracle Desktop External Support and can be accessed over the internet without the corporate VPN. Almost all downloads on the site are suitable for installation and are licensed for use on Oracle employee's personal systems. I have the site on my synchronised bookmarks and it comes in very handy.
Strange cloud heads for Iceland
Google appears to be always thinking about new tools or approaches to make or save money. Lots of these ideas sneak out onto the internet and lots of discussions, articles and opinions get generated. Occasionally, a real product is eventually seen. Way back in 2008 rumours about a Google data centre navy abounded. That particular Times Online article mentions some statistics and reports about data centres and carbon footprint which I have yet to verify. However, other articles and press releases have suggested the data is not without foundation. Here's a quote:
Data centres consumed 1 per cent of the world’s electricity in 2005. By 2020 the carbon footprint of the computers that run the internet will be larger than that of air travel, a recent study by McKinsey, a consultancy firm, and the Uptime Institute, a think tank, predicted.
It was with great interest that I read about a zero carbon foot print data centre being proposed in Iceland. The data centre will not be up and running until next year, but is being built on an old NATO base. Expecting to take advantage of free ambient cooling and 100% renewable electricity verneglobal are predicting substantial reductions in carbon released from day to day operations.
While a great idea, I feel the greatest speed bump in the migration to Iceland is regulation and legislation, or rather the perception of compliance with data privacy laws and in particular the Patriot Act.
Ireland's new Baywatch mashup
Due to a new initiative from the EPA you can keep up to-date on the water quality of Ireland's major bays (hence the article title), beaches and rivers. Made possible by some hard work from the clever people at IBM's Water Management Centre of Excellence, Splash provides a great way to research different beaches and decide where to visit based on a number of parameters — water quality, weather, and whether or not a lifeguard is on duty, and so on. You'll note from the spelling of Centre that it is European based. In fact it's current home is right here in Dublin.
The site is a clever mashup of EPA water quality data, which is provided by the local councils, some location data and weather reports from AccuWeather. There also appears to be a Twitter status check as well but I have not seen any data from this actually displayed on the site. The location data includes a description of the area and some images.
For the Oracle offices in Dublin, the nearest beach is Dollymount Strand. The Splash website provides the following description:
Dollymount provides tremendous respite from Dubliners from the vagaries of city living. It is along beach with sweeping views of the Dublin Mountains. This seaside area and wildlife reserve is located north of Dublin Harbour. The strand is connected to the shore by a late 19th century wooden bridge. Dollymount is on the seaward side of Bull Island, one of the most protected pieces of property in Ireland. Cars are allowed on a small section of this beach which is separated from the Blue Flag beach by wooden pilings.
I'm not sure how 'respite from Dubliners' is achieved. Anytime I've been on the beach, at least one Dubliner has been there. The images are also of great interest as the site provides a birds eye view that you can zoom in and out of as well as a photo of the location. No Dubliners, or people for that matter appear in the images, so perhaps that is the respite referred to.
One of the IBM blogs suggests that this form of mashup will be rolled out to other countries in the future. Personally, I think this is a great example of innovation within Ireland and I look forward to seeing more if it.
The site is a clever mashup of EPA water quality data, which is provided by the local councils, some location data and weather reports from AccuWeather. There also appears to be a Twitter status check as well but I have not seen any data from this actually displayed on the site. The location data includes a description of the area and some images.
For the Oracle offices in Dublin, the nearest beach is Dollymount Strand. The Splash website provides the following description:
Dollymount provides tremendous respite from Dubliners from the vagaries of city living. It is along beach with sweeping views of the Dublin Mountains. This seaside area and wildlife reserve is located north of Dublin Harbour. The strand is connected to the shore by a late 19th century wooden bridge. Dollymount is on the seaward side of Bull Island, one of the most protected pieces of property in Ireland. Cars are allowed on a small section of this beach which is separated from the Blue Flag beach by wooden pilings.
I'm not sure how 'respite from Dubliners' is achieved. Anytime I've been on the beach, at least one Dubliner has been there. The images are also of great interest as the site provides a birds eye view that you can zoom in and out of as well as a photo of the location. No Dubliners, or people for that matter appear in the images, so perhaps that is the respite referred to.
One of the IBM blogs suggests that this form of mashup will be rolled out to other countries in the future. Personally, I think this is a great example of innovation within Ireland and I look forward to seeing more if it.
Fear of maths is a problem worth solving
 According to researchers at the University of Granada, 6 out of every 10 university students present "mathematical anxiety". This study was carried out in a sample consisting of 885 first-year students from 23 different degrees given at the UGR which include the subject of Mathematics, both compulsory and core. The sample included four of the five university fields of study: Health Sciences, Experimental Sciences, Technical Education and Social Sciences. The conclusion is that many students choose 3rd level courses different to those they preferred - and in which they would be really good in many cases – in order to avoid studying subjects connected with Mathematics. Clearly there needs to be some help with math at an early stage in life to avoid this anxiety and help people get comfortable with maths.
According to researchers at the University of Granada, 6 out of every 10 university students present "mathematical anxiety". This study was carried out in a sample consisting of 885 first-year students from 23 different degrees given at the UGR which include the subject of Mathematics, both compulsory and core. The sample included four of the five university fields of study: Health Sciences, Experimental Sciences, Technical Education and Social Sciences. The conclusion is that many students choose 3rd level courses different to those they preferred - and in which they would be really good in many cases – in order to avoid studying subjects connected with Mathematics. Clearly there needs to be some help with math at an early stage in life to avoid this anxiety and help people get comfortable with maths. At first this may not appear as such a big issue for Computer Programming, particularly as the majority of the software development emphasis is on business rather than scientific solutions. It may be obvious, but it has to be pointed out that one of the key residual benefits from studying to solve math problems is the development of problem solving skills. While many of us , years later, may rarily use the algebra we study in school, the process of breaking down a problem into it's constituent parts stays with us when we go out into the real world. Where problems have vague specifications. Where there is more than one way to solve a problem. Where you run into problems you have never seen before.
At first this may not appear as such a big issue for Computer Programming, particularly as the majority of the software development emphasis is on business rather than scientific solutions. It may be obvious, but it has to be pointed out that one of the key residual benefits from studying to solve math problems is the development of problem solving skills. While many of us , years later, may rarily use the algebra we study in school, the process of breaking down a problem into it's constituent parts stays with us when we go out into the real world. Where problems have vague specifications. Where there is more than one way to solve a problem. Where you run into problems you have never seen before.There is free online math help available. To name just a couple there is:
- http://www.math.com
- http://www.mathway.com
Also there is a great book called Maths: A Student's Survival Guide which will be valued particularly by those who need to make up a deficiency in a specific topic or to remove the rust from their mathematics. If all this is too much to start working on your own mathematical anxiety then consider chocolate. At least you'll get something out of it!
What's the bedrock to your Social CRM Strategy?

Perhaps it is taken for granted, but Esteban Kolsky's recent article on The SCRM Roadmap, is missing the requirement for a Social Media Participation Policy for employees. No matter where you are on his SCRM pyramid such a policy is vital. The first thing it does is give an employee permission to use their own initiative and participate in customer conversations.
Experts
There are few better experts on your products or services than your employees. Apple Inc. makes a point of highlighting these Geniuses and puts them to work in customer facing roles. With the advent of Social Networking, your experts do not need to have such a specific role, but can still be recognised for their contribution in making their company great.
Permission to talk
Your company doesn't really have to have more of a strategy than permission to get started on becoming a social business. Moreover, a simple, publicly available guideline affords employees some protection from pressure to discuss or comment on topics that are not appropriate.
Guidelines
 It can be made clear that while all company employees are welcome to participate in Social Media, it is expected that all who participates in online commentary understand and follow some simple but important guidelines. This really is irrespective of medium (video, blogs, twitter, etc) and could also be applied to more traditional communication mediums such as the press. However, I'll stick to the internet based communication channels for now. These rules might sound strict and contain a bit of legal-sounding jargon. Some of the rules may be intuitive and considered basic common sense. However, please keep in mind that the overall goal is simple: to participate online in a respectful, relevant way that protects the company's reputation.
It can be made clear that while all company employees are welcome to participate in Social Media, it is expected that all who participates in online commentary understand and follow some simple but important guidelines. This really is irrespective of medium (video, blogs, twitter, etc) and could also be applied to more traditional communication mediums such as the press. However, I'll stick to the internet based communication channels for now. These rules might sound strict and contain a bit of legal-sounding jargon. Some of the rules may be intuitive and considered basic common sense. However, please keep in mind that the overall goal is simple: to participate online in a respectful, relevant way that protects the company's reputation.A great list of sample policies from existing organisations, some of which are written with industry specific rules, is available at Social Media Governance. It is well worth a read. The following is a guide highlighting some of the dos and don’ts covered in most of these policies.
DO:
- Protect confidential information.
- Respect copyrights.
- Be credible, transparent and identify yourself as an employee.
- Be in a position to offer comment from a point of clear knowledge of the subject matter.
- Avoid jargon by writing in simple terms.
- Use caution. While not all company employees are official spokespeople, please use caution in your comments as reporters and analysts may report on anything included in your online postings. Also, once online, the comments are cached, distributed quickly and available effectively forever.
- Secure approval. If you are an official spokesperson for the company, you must submit each posting to for review / approval before posting. If you are not a spokesperson, you will need to check with the company to determine if your blog and postings need to be approved.
- Make it clear that your views are your own and do not necessarily reflect the views of your employer.
- Comment on merger and acquisition activity.
- Discuss future product offerings, including upgrades, or new releases.
- Make growth predictions of any kind.
- Break out revenue by specific product or country.
- Use any inflammatory language or discredit others’ views.
- Provide headcount numbers for any country, region, group or department.
- Discuss customers that are not currently referenceable to the press.
- Provide the number of customers for a specific product area.
- Speak for the company.
- Lie.
Hosted Security Breakfast Seminar: Dublin
Staying on the topic of hosted applications and security I thought I'd bring this to your attention. MessageLabs, a Symantec Company, is organising a breakfast seminar on Hosted Security in Dublin, in November. Although I won't be attending, you may find the presentations interesting and maybe get a free croissant or two.
http://www.messagelabs.co.uk/seminars/dublin
http://www.messagelabs.co.uk/seminars/dublin