Arvind Jain
Thanks US Bank for all these appreciation eCards. Thanks Daniel Hoke !!
From: Daniel Hoke
Core Value: We power potential
Sunday was the official launch of the next best action engine. The NBA engine powers potential for U.S. Bank and helps us to stay a step ahead. This is new for U.S. Bank and very much on the leading edge for the financial services industry.
This project was initiated in 2015 and thanks to your work, it launched on schedule with all the expected features. This was a big undertaking, including having to first upgrade the CRM system to Microsoft Dynamics.
The point of all of my summary explanation is that the NBA launch is a big deal to U.S. Bank!
I am writing to personally recognize your role in making this happen. Thank you for your work behind the NBA launch!!!
Daniel Hoke

When it comes to issuing eCards no body beats US Bank
Sent: Tuesday, June 13, 2017 3:24 PM


From: Deepak Nair
Core Value: We stay a step ahead
Thank you for your commitment to helping us close out ETM testing. Because of your dedication, even on weekends to help us move this forward, we have delivered with such high speed and quality. This was a great sign of team work and dedication. Thank you for all the support and help!
Deepak
Marketing Operations Team – Mantra
During the conversations and presentation I realized that sooner or later everyone needs efficient operations to be viable. Big or small, Pre IPO or a public company, you need to be able to measure how you are doing and then only you can improve upon it.
With all the modern tools available, there is a lot of confusion out there. So it was a long conversation but here is a quick take away summary of my presentation in one slide below.
What else would you look at ? Please comment.
Image credits: Anthony Powell's article "Efficient Marketing Operations with Data Management"
US Bank executive team awards Cognizant Team on successful NBA Project Implementation.
Reality hits me home, with aging parents and uncertainties of life. I learn about OPLL
But a recent mishap accident with my father has made me realize that there are far more difficult and significant things in life than I had yet to confront and I was not prepared to handle it alone.
Diwali the festival of lights had just gone by and we were all in a cheerful mood. My brother and his family were back home in India and the grand parents were having a good time with grand kids. My dad has just returned back to India after a pleasant three month stay with me here in USA.
Then came the scary Halloween trick for me. On a fateful day of Oct 30th 2016, just after Diwali in Bhilai, India my dad slipped and fell and the back of his neck hit the swing base. It was not a major accident by external measures, no external bleeding or wound, but it was severe enough to compress the nerves to a point were he could not move or stand up. He was lying on the floor, lifeless and could not move his both legs and one hand.
He was fortunately able to make an audible alarm and was picked up , lifted and transported to hospital. He was immediately admitted to Bhilai Sec-9 hospital in Chhattisgarh, India. There it was diagnosed that he already had a case of OPLL () and this fall and immobility are symptoms of a final breakdown.
OPLL is a calcification of the soft tissues that connect the spinal bones which results in a narrowing of the spinal canal and compression of the cervical spinal cord.
The cause of OPLL is unclear and I could not get a certain answer from anyone, but was told that people of Asian heritage especially Japanese have a higher likelihood of developing OPLL. Also more men seem to be affected than women.
OPLL SymptomsMost patients with OPLL are asymptomatic with no symptoms at all, but others may experience mild pain and numbness in the arms and/or legs to complete numbness in the extremities. The symptoms are similar to those of cervical cord compression.
Treatment of OPLLThis depends on the stage of OPLL and in my case , my dad is at stage 4 and that is the severest stage. Conservative treatment like activity modification and exercises may help relieve the pain caused by OPLL but I was told that open spine surgery is required.
If pressure is not relieved on the spinal cord then future damage and loss of neurological function is very much possible. At sec 1 Bhilai hospital, my brother was told that this may affect respiratory functions as well. So they advised immediate surgery and there is a major risk when you open up the spine.
Since then in last 2 months we have gone through many things and are working on getting this thing taken care of. It is a big help that my brother is back home in India and can execute on many on site things. Simple things like opening zipper or buttons that we take granted for in life start to seem like mammoth tasks. What you can do in person on site, is a significant thing in such circumstances.
I would like to thanks and credit the following websites for some of my research. Indian Government portal surprisingly had a good amount of research papers at NCBI.
https://www.emoryhealthcare.org/orthopedics/ossification-posterior-longitudinal-ligament.html
http://www.medscape.com/viewarticle/739292
https://www.ncbi.nlm.nih.gov/pubmed/16306836
We have undergone surgery since then and in future articles I will share more details, but if anyone is in similar situation, I will be glad to share detailed notes. I was helped by many known and unknown people so my heartfelt thanks goes out to them and I plan to pay it forward.
Thanks
Arvind
Micro segmenting using Adobe Target leading to personalization
Realtime micro targeting is possible, in the same way as it is with any other type of CRM data - data is pre-loaded into Adobe Audience manager (AAM) and as soon as AAM sees that particular user in realtime, it can show specific segment messaging based on their segment qualification. They key here is how finely you define your segments. The more micro targeting you do, the more personal the message will appear.
The thing that is not realtime is sending CRM data to AAM, but once the data is dropped to AAM it is available later for real-time use after some sync duration.
Thanks for reading
Arvind.
How can companies prevent cyber attacks like that of Dec 2013 Target credit card data theft ?
 By now we all know that passionate hackers are very smart and they will always have a edge over whatever known systems we can create (Firewall, IPS etc). Even the best SIO (Security Intelligence Operations) team cannot possibly know of each and every malware in advance so a traditional approach of IPS or Malware detection based on signature is so stone age thing now.
By now we all know that passionate hackers are very smart and they will always have a edge over whatever known systems we can create (Firewall, IPS etc). Even the best SIO (Security Intelligence Operations) team cannot possibly know of each and every malware in advance so a traditional approach of IPS or Malware detection based on signature is so stone age thing now.What is behind these recent acquisitions by Palo Alto Networks and FireEye ? Domain Talent and Virtualization
A day in Kunming China
Pricing strategies for services
1) Cost Plus
2) EVC (Economic Value to Customer)
3) Competitive Marketplace
2) Break down your costs into buckets (Server, support, manpower, gas, commute, task time, delivery model and expertise) and then have a variable formulae based on weightage to what you have in plenty and what is scarce for you.
3) Research your industry (business cycle, technology trend)
4) Research your customers (segment the market, are you their strategic partner, long term potential).
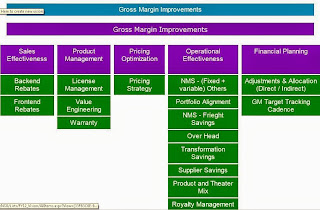
Five pillars of Gross Margin Improvement
When growth comes to standstill or products start to become commodity …nothing else matters as much as maintaining your Gross Margin.
A company can have stagnant revenue but Wall Street will still reward it's shares if it show profitability growth and how do you do it? Look no further than Gross Margin.
Essentially the five pillars of Gross Margin improvement are:
- Financial Planning
- Operational Effectiveness
- Pricing Optimization
- Product Management
- Sales Effectiveness
Operational effectiveness as a Gross Margin tool
The 8 top most things that come to my mind when we look at GM in high-tech industry from an operations perspective are (in no order of importance).
NMS - (Fixed + variable) OthersPortfolio AlignmentNMS - Freight SavingsOver HeadTransformation SavingsSupplier SavingsProduct and Theater MixRoyalty Management
We will drill down into each some other day in a white paper.
How is SaaS Product Management different from traditional Product Management?
2) Additional security around Access & Authorization
3) You earn your money every day and every moment, so it is not a traditional sell once and forget till the next new producty is available. If you fail customers may not and will not renew the subscription. So you have to develop SaaS with some stickiness feature like creating a website with lowest bounce rate and higher CTR (click through rate). so that there is highest probability of customers renewing.
4) Special considerations for On Demand / Multi Tenacy of the product / solution.
5) Much higer emphasis on Disaster Recovery, Peak Load and High Availablity.
6) One size does not fit all, so how would you provide innovation in cloud? How to empower customers in cloud so that they can maintain their cuttting edge by intelligent customizations.
MIT South Asian Alumni Association - MBA Panel Discussion
http://alumweb.mit.edu/upload/AS/MBA_event_flyer_26414.pdf
Some very interesting Web 2.0 Links that can help in Smart Marketing & positioning
- Google Trends - find temporal trends in search word usage on the internet
- Google Insights for Search - estimate relative importance of search terms with trends by geographical regions
- Google Analytics - web analytics solution that gives insight into your website traffic and marketing effectiveness
- Quantcast - monitor website traffic and effectiveness of marketing communications to customers. This give Demographics info of Visitors. You can also use Microsoft AdCenterLabs to analyze demographics.
- Hitwise - ISP data, can be used to analyze how people get to, spend time in and depart from websites, large sample size
- Alexa - web traffic metrics based on voluntary anonymous tracking of people who have signed up for free, large sample size
- Comscore - web traffic metrics based on voluntary tracking of people who have signed up for a fee, gives much more detailed information but sample size is small
- CrazyEgg - Click density analysis, find out where people are clicking on your webpage (is your design driving people to the right place?)
Landmark achievement for my team - Cisco announced as overall winner for SOA implementation award by CIO magazine and SOA Consortium.
Cisco SOA Team Wins SOA Consortium / CIO Magazine Award
Cisco was recognized by industry experts for its SOA initiatives, platform and implementation successes.
The SOA Case Study Competition highlights business success stories and lessons learned to provide proof points and insights for other organizations considering or pursuing SOA adoption. The contest was open to organizations of all sizes, including government agencies that have successfully delivered business or mission value using an SOA approach.
How to configure Standalone Fuego BEA Aqualogic Oracle BPM Studio to work with Secure Web Services?
Switched from Oracle BEA BPM Enterprise Version (on Weblogic) to the Standalone Version for Evaluation Purposes.
At end of last Tuesday I made a call to switch to Enterprise Standalone but the efforts put in were good learning and useful for Standalone Installation as well. So for the purpose of proceeding with evaluation going forward I have shifted to Enterprise Standalone Version as my focus is BPM.
Some learnings or observations .... On the Oracle website they refer to downloading Oracle BPM <?xml:namespace prefix = st1 />Enterprise Administration Guide.pdf but in real scenario there was no such file name. I realized that it was same as Oracle BPM Admin Guide.pdf and the same goes for configuration guide as well. So will not get confused in future :)
Ok so with the ultimate aim being to Deploying and Publishing a New BPM Project I had to go through a series of steps. (For standalone I needed a much smaller set but the practice and drill was worthwhile learning in terms of infrastructure and operationalization of product.
The whole list of steps:
- Creating Directory Service ( need to configure Directory Database Schema)
- Creating a Process Execution Engine ( need to configure a separate Execution Engine Database Schema)
- Configuring Weblogic Server
- Creating Weblogic Server Domain
- Create Oracle BPM Deploy User
- Installing Oracle BPM Deployer
- Creating JDBC Data Sources on BEA Weblogic Server
- Creating JMS Server, Module & Resources
- Configuring the Deployer and Deployment Targets
- Enabling Clustering
- Building and Deploying Application EAR Files
- Deploying and Publishing a New BPM Project
As of now I have Standalone Enterprise BEA BPM configured with Directory (Oracle 10g DB). Engine DB configuration has some issues due to privileges. Make sure you have a friendly DBA to help out.
I am trying to come up with a set of use cases to test out different features.
More next week as I try to put together a list of features .. dully prioritized that I will like to test out.
If you have a challenge for me ...Bring it ON :)
Currently evaluating Oracle BPM 10gR3
For the next one month I want to be critically evaluating Oracle BPM 10gR3.
Yes this is the new face and name of BEA Aqualogic BPM 6.5 , now with Oraclelization it is called as Oracle BPM 10gR3. Too early to make a comment.
My aim is to see how well Oracle has leveraged and integrated the BEA Aqua logic BPM products with its other products to offer a complete suite.<?xml:namespace prefix = o ns = "urn:schemas-microsoft-com:office:office" />
Getting started was easy .... Installed Oracle BPM Studio 10.3.0.0.0 from the link below. To get started
Please visit: http://www.oracle.com/technology/products/bpm/index.html
Here you will find download link – for initially getting your feet wet purposes, download of studio should suffice. Also, there is a tutorial and link to docs.
Installation was smooth, took around 60 Minutes. I referred to this site for the product documentation
http://download.oracle.com/docs/cd/E13154_01/bpm/docs65/index.html
One glitch ....
It took me 20 minutes to figure out why the "Launch Workspace" icon was disabled. Figured out that after designing the process I had unfortunately clicked on either "outline" or the "Log Pane" that exist below and clicking on those panes dynamical change the Menu and disable certain icons.
More later
Arvind